In this tutorial, you'll learn how to utilize John the Ripper to crack passwords for Windows 10, 8, and 7 on your local PC.
John the Ripper is an offline password-cracking tool designed to assess password strength, conduct brute-force attacks on encrypted (hashed) passwords, and execute dictionary-based password cracking. In simple terms, John helps in password cracking.
Disclaimer:
Please be aware that the techniques and tools discussed in this article are meant for educational and ethical purposes only. Unauthorized use of these methods to gain unauthorized access to computer systems or networks is illegal and unethical. Always seek proper authorization and follow the laws and regulations of your jurisdiction. The author and platform do not endorse or support any illegal activities. Use this knowledge responsibly and within legal boundaries.
Remember, with great power comes great responsibility.
Obtaining Password Hashes from Windows
The initial step is to extract the password hashes from the SAM (Security Account Manager) file, a Windows 10/8/7 database storing user passwords in encrypted form. This file is typically located in the following directory:
C:\Windows\system32\configTo extract the SAM files, open a command prompt (cmd) on the Windows machine and use the following commands:
reg.exe save hklm\sam C:\sam.save
reg.exe save hklm\system C:\system.save
These commands retrieve the password hashes from your system and save them in the C:\ drive.
Now, you should copy these two files (sam.save, system.save) and switch to a Kali Linux machine or another Linux distribution. Paste the files on the Desktop.
To view the hashes from the files, use the following command in the terminal:
impacket-secretsdump –sam sam.save –system system.save LOCALYou'll see the user accounts and their corresponding hashes. For this example, I will attempt to crack the password for the user "John."
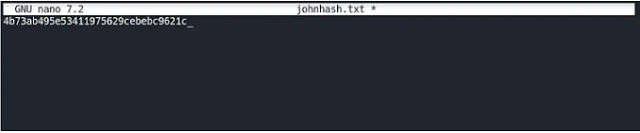
To do so, I'll copy the hash (e.g., 4b73ab495e53411975629cebebc9621c) and create a new text file using the nano text editor:
nano johnhash.txtPaste the hash in this file, and don't forget to save it.
Cracking the Password
In this step, I will use John the Ripper in wordlist mode to crack the user's password. In this mode, John can read passwords from a text file that you provide.
For this example, I will use the rockyou wordlist, which can be found in Kali Linux at /usr/share/wordlists/rockyou.txt. To initiate the cracking process, use the following command:
john --format=NT --wordlist rockyou.txt johnhash.txtHere, "rockyou.txt" is the wordlist file from Kali Linux, and "johnhash.txt" is the text file where I've placed the hash for the user "John" using nano.
As seen in the output, John the Ripper has successfully cracked the password, which is "letmein."
Final Thoughts
John the Ripper is arguably one of the most well-known password cracking tools in the world. It's frequently used by penetration testers and, regrettably, by malicious hackers due to its versatility and user-friendliness.
Note: Please be aware that this information is intended for educational purposes to expand knowledge and not for malicious or harmful purposes.
Follow Request:
If you found this article insightful, consider following me on Medium and visiting my website for more cybersecurity and ethical hacking content. Stay updated with the latest techniques and tools to enhance your knowledge and skills in the digital security realm. Your support is greatly appreciated!
Thank you!










1 Comments
I have a working relationship with XAP Credit Solution and am also one of his success stories. He’s quick to respond with questions and knows his stuff. Let me start by stating that I have been a mortgage broker for nearly 15 years; so you can only imagine how many credit reports I have reviewed in that time. Here is a fact – not everyone has had perfect credit including myself. There are always different circumstances that land people in their current situation but you always have a choice to do something about it. When it comes to credit repair; I have referred a number of clients and friends to XAP with great results. I, for one, would not send personal friends to someone unless I had 100% confidence that they would be treated well and the results were proven. After seeing how well XAP’s program worked for my customers; I decided to move forward with my own credit repair. I strongly recommend XAPCREDITSLUTION @ G MAIL. COM to anyone in need of credit repair.
ReplyDelete